4
Onit Website Design

9
Onit ebook

8
Data Archiving White Paper

13
ContractWorks ebook

7
A10 Ebook

9
DDoS Attack Types

9
Evolution of the online battlefield

7
Application Intelligence Report

4
Social & Web Page Banners

5
Armor Playing Cards

6
The Fight for Creative IP

3
Enterprise Legal Reputation Report

1
Insider threat infographic

2
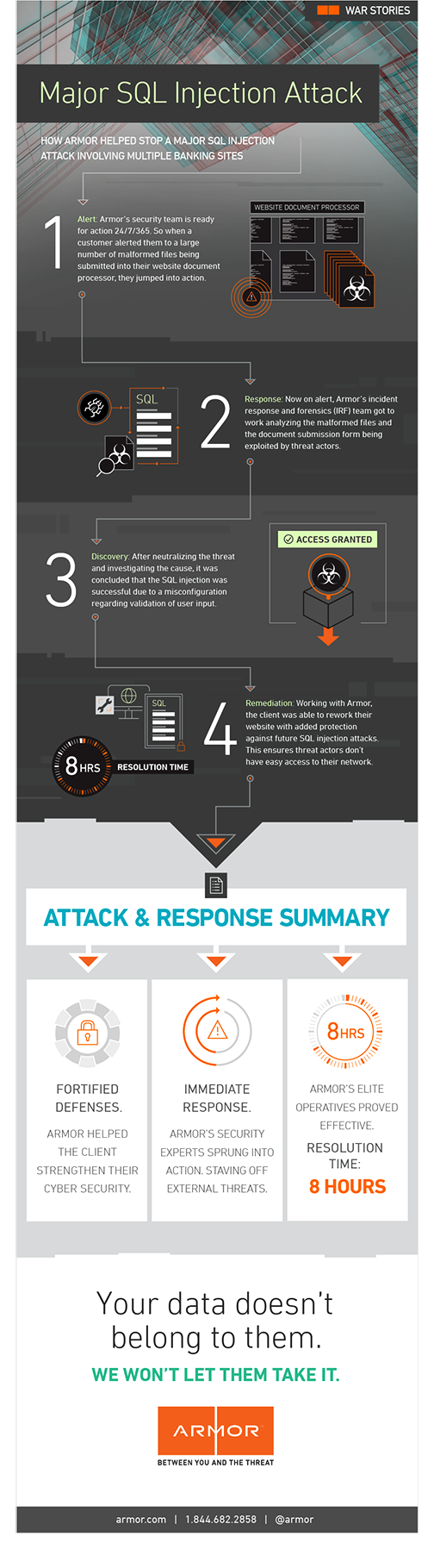
Armor War Stories

1
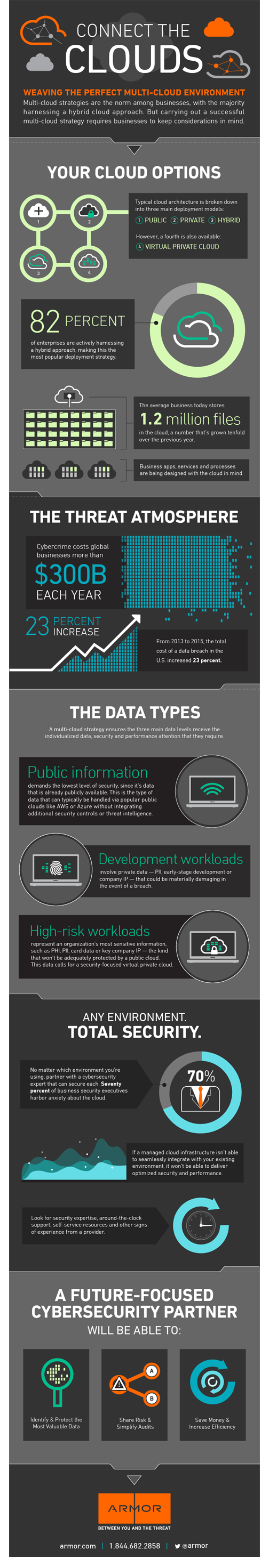
Connect the Clouds

1
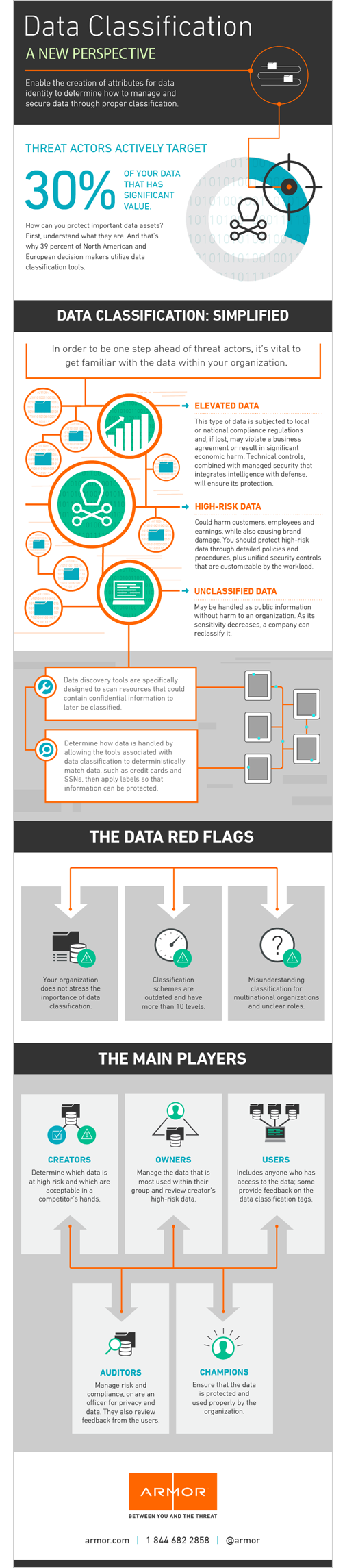
Data Classification: A New Perspective

5
Promotional T-shirts

3
The Original Oklahoma Breakdown

4
TRU - Threat Resistance Unit

3
Events Landing Pages

4
Game Over - Your Compliance Checklist Amuses Me

1
Threat Intel Brief Ad

1
Bodhala Print Ad

2
Kitchen Design Concepts